Quick Reference Guide:
Wow, the world is shifting fast! On the other hand, many of us have been naming and ringing the alarm about the rise of fascism, late stage capitalism, and the collapse of the US Empire for some time now. So this insurgence of technocratic and authoritarian rule with draconian policies and tactics seems late. Either way, it is here now and ramping up quickly.
The law may reflect morality, but the law is not inherently moral. The law may reflect justice, but the law is not inherently just. We are under no moral obligation to honor any unjust law. In fact, our moral obligation is to challenge any and all unjust laws.
With all that is popping of in Los Angeles, Minneapolis, Chicago and other places many on the left (a term loosely used) are preparing for all out confrontations. I keep getting asked how to resist, what to resist, and how to stay safe while doing it. First things first and just to get it out in the open, there is no such thing as “safe.” All we can really do is slow our opposition down by creating more safe ways of communicating and showing up. There are steps we can take to decrease or inhibit the tracking, doxing, and other nefarious forms of information gathering.
There are two directions of communication that we all need to be cognizant of, but most people are only concerned about one, that is, their communications being intercepted. However, we also need to be concerned about the information we are receiving. What makes it trustworthy? How reliable is it? Is it temporally useful or is it late? I will dive more into that later. For now, I will focus on securing comms from leaks.
On Phones
One of the things that people are asking me is whether or not to bring phones with them when engaging in resistance efforts and my boilerplate response is that it depends. It depends on what your needs are and how well prepared you are to enact alternate forms of sharing information. It also depends on what measures you have taken to protect your devices from from intrusion and interception. Remember that nothing is ever completely secure or safe, only more or less so. Also remember, that in most cases and for most people, no phone means no communication, no real-time updates and no real-time calls for assistance.
Backing up for a moment to explain why many people are concerned about whether or not to bring their phones with them to protests, actions, or other resistance events is in large part do to tracking. Cell phones use cell towers, which are pretty much ubiquitous throughout the united snakes. You are like, “well duh…” but, many of the things that have made our lives “simpler” have also made us more vulnerable, though. Phones, music players, cameras, and GPS units used to be four separate devices that we needed to carry with us. Now they are all built into one device and the software has interwoven all this hardware in the programs.
Additionally, our phones (and other devices like tablets, computers, smart watches, and the like) transmit the data from those programs and hardware back to the cell providers. Each time we download or activate an application there is a “permissions” disclaimer that pops up and most people, who are likely on autopilot at this point, simply click “accept” because we are taught to believe that it improves the functionality of our apps and thus our devices. Well, surprise, doing this grants permission for those companies and corporations to access your data at will, like your biometric data from your wellness app tracking your sleeping patterns, your heart rate, your blood pressure, your exercise patterns, where you exercise, and who you exercise with. Creepy, right? Like, what are they doing with all of this data?
Going a little further, like a home address that specifies the exact location where a person resides, the internet requires and utilizes IP addresses to identify the specific computer transmitting and receiving data, and phones and hotspots utilize what is called an IMSI number, the International Mobile Subscriber Identity stored on the SIM card and which is the address of your device. Because cell phones have all the hardware and programs interlinked, when a cell phone is pinging off of a cell tower, the specific address of the phone is identified, as is the location. What this means is that when a cell phone or other device that is broadcasting enters into a the region of a cell tower, it is being tracked. This information is also stored by the owner of the cell tower.
Most of us have received an “Amber Alert” or a “Severe Weather Warning” or something to that nature. Ever wonder why you are not getting updates from the other side of the country, if everyone is receiving these updates? Geofencing is the reason. Geofencing is a digital zone which represents a physical location like say a city, or a neighborhood that telecommunication companies use to target the people in a region with adds, or the government uses to issue warnings to the people in a region who need it. They do this by tracking all the IMSI numbers that are pinging the towers in the selected zone.
All of the above about cell phones is going on all the time and happening to nearly everyone who carries a phone with them. Now add to this equation a protest, a direct action, or acts of resistance and I am willing to bet you could imagine the increased motivation of law enforcement to deploy such tech against the people. Well, Federal regulations require telecommunications companies comply with “lawful orders” to surrender control of or access to information from their cell towers. This means that not only do the telecoms have access to your data, but so does law enforcement and the feds. This is partly why people are concerned about bringing their phones to actions.

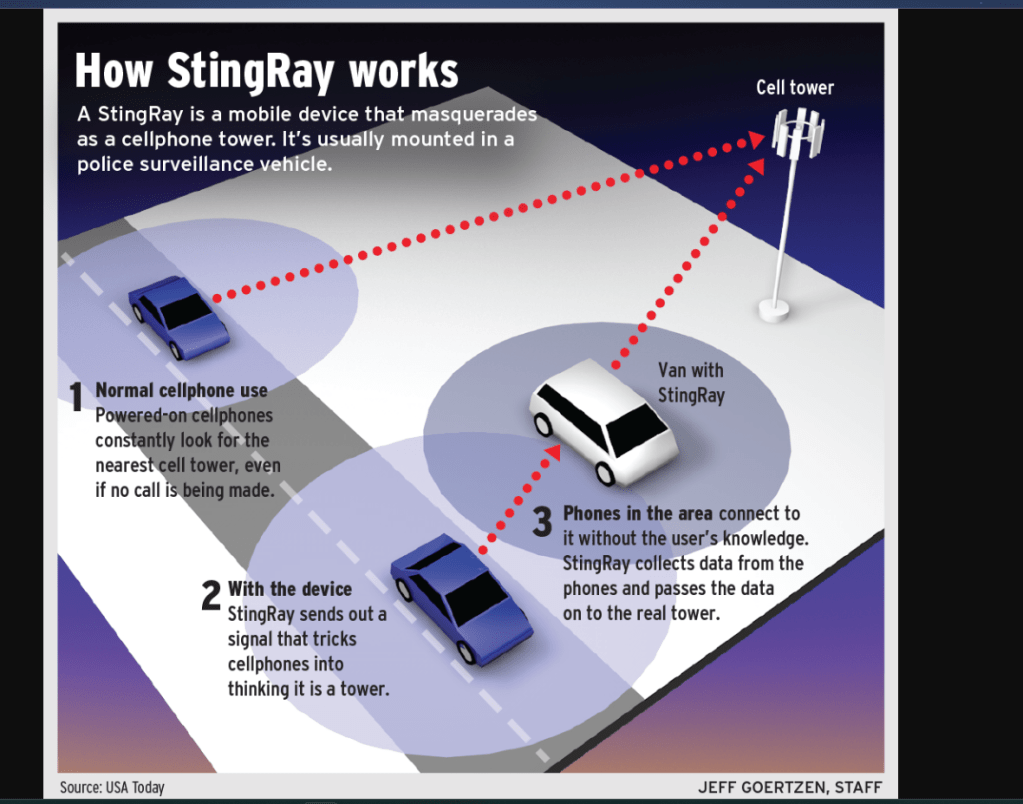
Additionally, law enforcement, the feds, and other nefarious actors commonly have access to and deploy what is known as a Stingray. Stingrays and units like them simulate cell towers. The way cell phones work is that they ping the nearest cell tower. Well, if there is a simulator cell tower closer than the actual cell tower, then the phone or other device will ping the closest first. The stingray intercepts the signal and data from the device and forwards that to the actual cell tower. With the stingray they trick the phone into sharing the IMSI of the phone along with the location data. For most phones, the IMSI is attributed to the owner of the phone via the service provider, like T-Mobile, Sprint, AT&T, Verizon, Boost Mobile, Metro PCS, etc… Additionally, they can intercept location data and can open and read unencrypted SMS messages (texts) gaining access to images, audio, videos, files and more, and can listen to unencrypted calls.
Phones and other devices have more vulnerabilities via the Wi-Fi and Bluetooth connectivity, with the latter being the most vulnerable to attack. We use both Wi-Fi and Bluetooth to connect to other devices like watches, pacemakers, insulin pumps, heart and blood sugar monitors, headphones, cars, Ring Doorbells, the lights in our homes, Alexa or Siri, computers and tablets, the list goes on. When Wi-Fi is turned on it is continuously searching for other Wi-Fi connections, which all have IP addresses connected to physical locations. This constant connectivity is used in conjunction with GPS, which uses satellites to triangulate location, the Wi-Fi provides a precise location. The security protocols for Wi-Fi are much less secure than cell signals and easier to crack, and this holds even more so for Bluetooth. If one of these signals is hacked, then the hacker can do anything from viewing and mirroring the device screen to pillaging the device for data, infecting and corrupting the device, or using the device via accessing the contacts to send malicious or false messages to your connections.
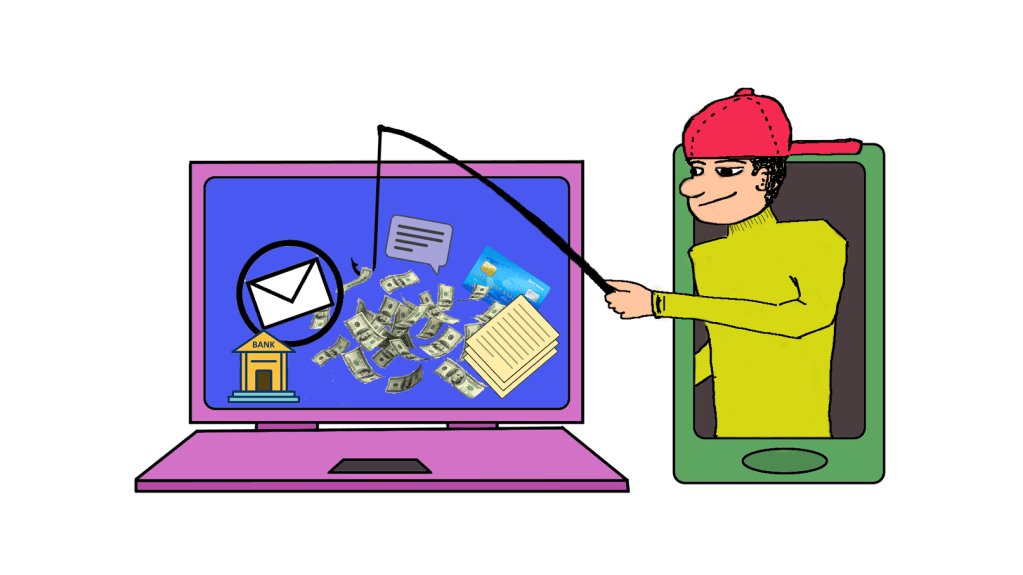
Currently, the best information we have is that say a phone or device is being monitored via a geofence or stingray, they are only able to view or access the “unencrypted” data. What is not clear at this point is whether if the phone has been hacked into via the Wi-Fi or Bluetooth, whether encryption apps like Telegram, Signal, Jitsi, or Proton prevent or otherwise protect from screen mirroring. What is clear is that via the geofencing, activist are being targeted by phishing and spear phishing campaigns. Phishing is the sending of a bait and hook message, usually with a link embedded in the text. These messages look real, they look authentic, but there are usually indicators that they are not. Often the grammar will be off or the link will look strange upon inspection. In the case of one of your comrades phones being hijacked, the Phishing may see to come from someone you know. Usually, this is the way in which a phone or device is hacked. It is not through some tech-wizard busily typing on a keyboard, but merely by getting one of us to click on a link, which grants them permissions into our devices.
These are many of the reasons that people are concerned about whether or not to bring their phones or other devices to actions or resistance events. Even knowing all of this I still say that it depends. It depends on what your needs are and how well prepared you are to enact alternate forms of sharing information. It also depends on what measures you have taken to protect your devices from from intrusion and interception.
Suggestions for Securing PHONES & Other Devices
- Purchase a reputable anti-virus software for your phone and scan it and the apps you have on it often.
- Purchase a reputable VPN (Virtual Private Network) to mask your IP Addresses, put it onto your phone and your other devices
- Check the permissions you have granted to all the applications on your devices and limit them wherever possible. There is no reason that the calculator app should have access to your location data, and if you do not want to be sharing your health information with your telecom provider, turn that off, too. Many apps will want permission to share bug and usage data. You can turn that off, too. Perhaps most importantly, watch for apps that want to have universal access to your microphone, camera, and contacts. The Facebook Messenger app is notorious for this.
- Many of our phones, although, not all of them, have settings that will permit you to completely shut off access to both the camera and microphone to all applications on your phone. It functions much like the “airplane mode” function being that you can toggle this setting on and off as you need to.
- Download, install, and use encrypted services for your texts, calls, video chats, emails, and document creation. For example, the Signal app is the standard right now for for text, calls, and video chats/conferencing. CryptPad and Proton Drive a good encrypted alternatives for document creation like word processing, spreadsheets, and presentations. While they may not be as user friendly or intuitive as say, Google Drive, they are more secure and not volunteering to share your information with the feds.
- Set and use the disappearing message function religiously.
- Update your phone as often as updates are available for it. This will help to scrub your phone of most malicious attacks, as they were designed for an earlier version of the Operating System (OS).
- Restart your phone often. Surprisingly, this will cause a reboot and reinitiate the OS removing some malicious attacks as well.
- Be frugal with your Bluetooth and Wi-Fi. Do not just leave them on because it is convenient. Instead, turn them on as you need them or as you intend to use them and then turn them off when you are done.
- Turn off biometric access to your devices, that is, facial recognition and fingerprint unlocking and accessing. It only seems more secure, but all someone has to do is put a picture of your face in front of the device and it will open, or use your finger (against your will) to unlock your device or the apps contained within.
- Use a password or pass phrase to unlock your device and the apps within that is at least 10 characters long. It is better if it is alpha numeric with symbols. Remember, the longer and more complex, the harder to crack, but also the harder to access.
- Download and use a password manager. Stop using services like FaceBook (fedbook) or google to log into your accounts and store your passwords. Those platforms are not only insecure, but they do not have our best interests in mind. We have passwords for everything, like bank accounts and stores, and libraries, school, work, etc… and it can be impossible to remember them all (if you are using one password for multiple accounts, stop now and create new distinct passwords for each of those accounts). This is where a password manager comes in handy. Currently, the recommendation is for One Password because their encryption has not been hacked and the information has not been breeched. This may change in the future, so do your research and do it regularly.
- Download and use Two-Factor-Authentication (2FA) services to protect your most important apps and accounts, then go to those apps and accounts and turn on the 2FA, linking them to your 2FA application. This will alert you to someone else trying to access your stuff, and hopefully prevent them access long enough for you to changes the passwords to them.
- If you are going to use social media or similar platforms and you are going to share images, videos, audio files, or other documents then be sure to manage your METADATA as well as what you can readily observe in the files themselves. Be weary of any visible identifying information making its way into your photos and videos. Additionally, scrub the metadata that likely contains location data, IMSI or other identifying data, and the like. When a file is transferred it carries with it all the metadata. Signal has a default setting of scrubbing metadata from photos, videos, and audio files. You can load it to yourself and then share it if you must. There are more complex bulk tools you can use, but they are complex and you can research those yourself.
It’s true, that several of the recommendations above come with an upfront cost, but I encourage you to consider that either you pay for the product, or you are the product. Furthermore, the upfront costs are highly likely to be much less than the costs and stress of someone gaining access to your accounts.
Before leaving the matter of phones it is important to name two other vulnerabilities of concern, both of which were created by Israeli companies. The first is Pegasus and the second is Paragon. Pegasus is a military grade spyware that can hijack a phone without anything being clicked by the user and all that is required is proximity to the devices. Once the first device is infected, it can then infect all other devices that it enters the proximity of and this will continue until the intended device is infected. Pegasus has the capacity of all the malware listed above such as mirroring, pilfering, and transmitting information to others, but not deciphering encrypted data. Paragon on the other hand is a much newer and more powerful military grade spyware that can decipher encrypted data as will as enact the other harmful elements of malware. The united snakes has purchased subscriptions to both of these spywares posing a significant threat to positive building organizing and resistance activism. It is not currently known how Paragon is spread and I have currently not come across either a way to detect or to remove it. Pegasus on the other hand can be detected and removed with some additional software that you can find and download if you suspect something is wrong.
Ground Comms
If you have considered the variables and taken the steps to secure your device and accounts and you chose to bring your phones with you because the situation is such that you need the real-time communication, then consider the following:
- A fair practice is to turn off Wi-Fi, Bluetooth, and GPS. Airplane Mode “should” stop cell tower communication and still allow you to take photos and videos, but Bluetooth and Wi-Fi may still be active.
- Delete search history
- Delete past location history
- Only communicate on encrypted platforms and set you messages to “disappear”
- long password protect your device
- If one of the people in your crew is abducted by the authorities and part of your on the ground comms strategy includes Signal (or similar) encrypted message threads, burn the thread and make a new one that person does not have access to because there is a high probability your comms will be infiltrated.
- If your phone is seized:
- Don’t consent to a search
- Don’t unlock your phone
- A lawyer can file a motion for the return of your property if it is not being held for evidence
- If you remotely revoke access to services or delete information on the device that may be considered “obstruction of justice” or “destruction of evidence” and there may be charges filed as a result
- Let your people know so they are not active in vulnerable or exposed chats
Better yet, get a burner phone and do all that anyone, plus the other phone safety precautions named above. A couple of reasons in addition to the tracking and identifying elements for considering a burner phone include a need or desire to limit access to your connections and/or data if the device is lost, stolen, or confiscated. Yet, remember, that for it to be useful in real-time, while On-The-Ground (OTG), you will need to have some of that on the device. Also consider getting a faraday bag for the phone so that you can put it away when you do not need it, blocking all transmission signals to and from your phone/device(s). You are going to need a faraday bag to get and safely store the burner phone anyway because you do not want the burner and your actual phone being pinged in the same place at the same time (i.e. together) because then it defeats the purpose of having a burner. Make sure to install the encrypted services you need on the phone so that you can communicate more securely. To get the phone started, you will need to create a new email and this is best done from an IP address that is not connected to you or anyone you know. You will then need to create a secure email from the device in that same location so that you can begin to download the apps you need. Remember to set all the permissions of the device to keep yourself the most secure and private.
The only secret that stays a secret is the secret that is never shared. Nothing is ever completely secure. If the information is absolutely something that you would never want someone else knowing then it should not be written or uttered or otherwise displayed in digital tech, encrypted or not.
One of our greatest vulnerabilities is not that one of our devices will be hacked, but that an agitator, a spy, or the authorities will simply be let in digitally or physically.
And how many fights have started because a “screenshot” of what someone wrote or said was shared outside of the intended audience? As such, we should not be sharing sensitive information in unvetted chats or meetings, or discussing subjects in-person and out in public very cavalierly because we never know who is watching and listening. Vetted chats and meetings with vetted people are more secure but err on the side of caution when considering whether the information should be written down or recorded. Save the most sensitive stuff for in-person conversations or just keep it to yourself.
Keep in mind that not everyone needs or should receive or have access to the same level of information. Most of us are not in the habit of blurting out our latest STI checkup all over social media especially, if we received some unhappy news. Most of us also don’t pass around our latest bank statements to the people on the bus. Conversely, most of us would yell “FIRE!” if people were in danger, or “ICE!” or “la Migra!” if armed, gestapo, neo-brown-shirt agents were invading our neighborhood. We choose the audience for information all the time and organizing and activism should be no different.
Consider the following graphics of both Onion Organizing and Snowflake Organizing models:
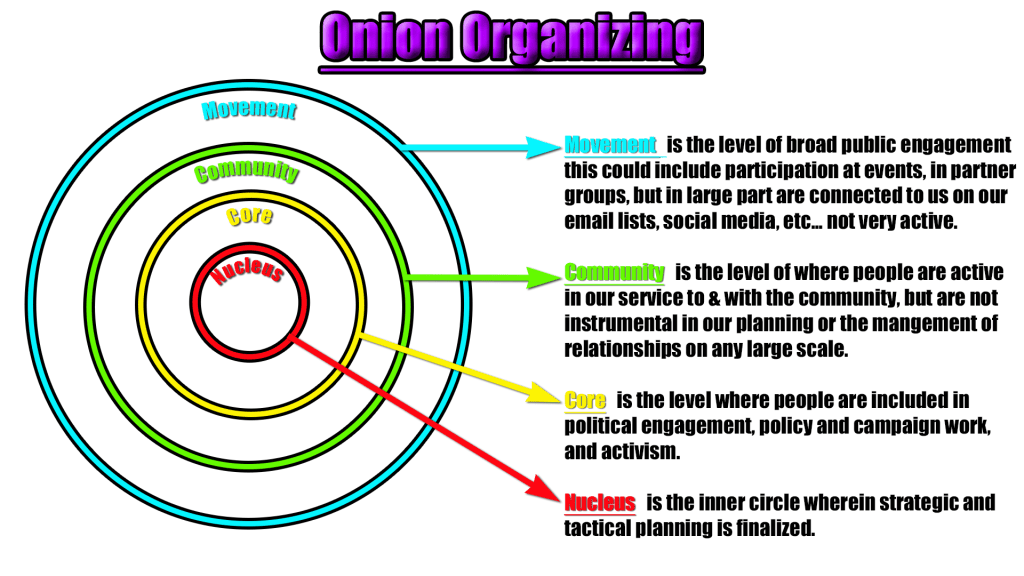
The onion organizing model not only provides a visual of people’s involvement and commitment, it also lays out some security culture and opp-sec parameters. This holds whether it is a thread, an assembly, or a protests. Not everyone is one your side and certainly not everyone has the same concern for privacy that you do. The categories are termed movement, community, core, nucleus and can be thought of in terms of messaging protocols. Imagine if you will that information is shared in the nucleus, for the nucleus only, and someone in the community sphere learns of it. To make this example less heinous, let’s further suppose it’s your mom, whom you were just having a good time catching up with and who you know has no interest in harm coming to you. Notwithstanding that, the info you shared was time sensitive about an upcoming surprise visit somewhere (perfectly legal, but unwanted by the target ). Now lets assume that mom shares her excitement while chatting with friends at the local cafe after working out and some people not in any of the onion categories overhears, who then share that information with people who share interest with the target of said surprise. Well, it will no longer be a surprise. Nothing nefarious happened, and there was no ill intent, but damage was done all the same. Now lets consider that a provocateur is attempting to work their way into our information chain, it could be a fed, it could be a sad-boy, it doesn’t matter. The onion model also reflects “circles of trust” and lend itself to a vetting process. Everyone’s process will be different and I highly doubt that any will be perfect, ever. These large Signal, Whats-App, and Telegram threads that are popping up all over because people started catching onto the trap of social media organizing are absolute cluster fucks that obliterate the vetting process and circles of trust. There is no way of knowing who is in the space. To make matters worse, people are being moved from large threads into more tight nit threads, and people with no opp-sec or security culture practices are vouching for people they have no business vouching for. Can anyone say “INFILTRATED” ?
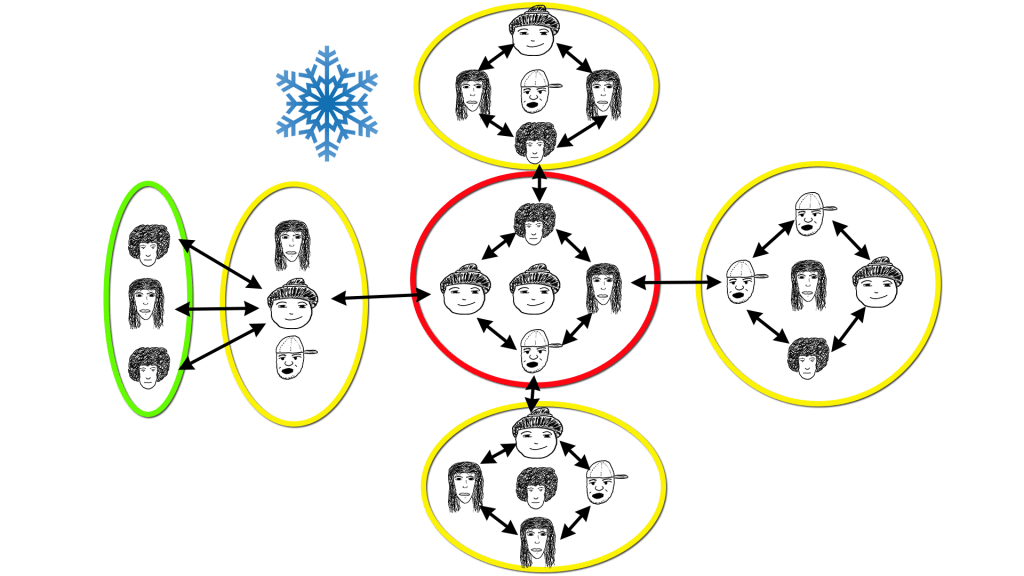
Which brings us to the snowflake organizing model. (The colors in the two diagrams are meant to work together for ease of reference.) The inner-circle is buttressed by a close ring of other circles. In terms of trust, the yellow layer has earned a lot, but still does not need to know everything. Perhaps the situation is such that there are multiple affinity groups doing different direct actions that will work in concert, but it is possible that a sacking of one could lead to a sacking of the others if too much information is shared too broadly. Perhaps the risk levels, self-selected, by those in the yellow-sphere, relate to narrative shift, non-arrestable negotiation type work and while on-board with more direct confrontation approaches, cannot for reasons of their own be part of it. The Red-Team, which in this example can also relate to the Green-Yellow-Red Risk Levels of equitable organizing, has a higher risk level and is employing a diversity of tactics to the campaign strategy. Their need for increased privacy and directive capacity is higher than the yellow-sphere.
The snowflake model also lends itself to equitable distributions of labor. Not only is it impossible for any one person to do the lifting of an entire campaign or action, it is also not possible for one small group to do it all. There are comms, planning, art, messaging, networking, coalition building, fundraising, etc that all need to be handled. Breaking that up into teams is necessary for the life of your crew. This of course skirts the issue of information leakages without good practices and expectations built upon equitable agreements, in place.
Putting all of this together, whether you are in the nether world of the digital-sphere or OTG at some event it is very important to be clear about what information you are sharing with who and why. A good maxim is that if you met in-person, in a place without microphones and cameras, and you did not have your devices on you, then it is probably a good idea that it is not discussed in public or on tech. If you do not know who is in the space, or you do not know everyone in the space (i.e., large Signal threads), then perhaps that is not the place to share everything you want to share. Even if it doesn’t have infiltrators, it will likely have well-meaning-folx who merely have not been steeped enough in the practices of security culture and opp-sec enough to be trusted with secret or detailed planning information yet.
If you choose to leave your phones behind, the consider the following:
The vulnerabilities and security risks named above certainly present many reasons for us to part ways with our digital devices, but that decision comes with the cost of slowing, shrinking, and minimizing communication. A way to get around this shortfall is to use radios.


However, radios can be listened in on much more easily because all someone has to do is scan the open frequencies until they find the frequency being used. If radios are the selected alternative then being aware of this vulnerability is essential. As such, must more opp-sec is required than even unvetted chats and meetings. Developing code and short-hand may be necessary. Either way, strategic elements and personal or otherwise identifying information should be protected. The only identifying information that should be going over the radio channels should be about provocateurs and threats to our safety. Code names are an essential OTG practice, but are pretty much necessary for radio comms. Two-Way-Radios have a limited zone of usage, especially in a city where there are structural interferences such as concrete and metal, so while it is possible to identify a voice, record it, and use it to place a person active in a region at a particular time, it is not like a cell phone which can provide an exact location moment to moment with the identity of the person. Now there may be a world in which the left deploys encrypted radios, which are often digital, but the use of encrypted radios is illegal (i.e., not legal for us). If the authorities are out and watching and see people on radios they cannot intercept, that will likely throw up a lot of red flags about them and may provide additional impetus for them to interfere. It is a Federal Communications Commission (FCC) violation for the general public to use encrypted radios without a license, and the license comes with specific requirement about how and when they may be used. The choice is yours of course about when and what type of radio to use, but you should at least know the different risks. A standard 2-way radio will often be able to access frequencies that require a license to use, but they also access the Family Radio Service (FRS) frequencies that do not. As of right now, we have not seen too much interruption and interference with people using the standard two-way radios on most of the frequencies they can access, but there have been utterings of a crackdown looming.
A word of caution, it is okay to monitor emergency bands and frequencies, like police or fire stations. but it is illegal to interfere with them. Someone’s life may be hanging in the balance.
Another way and often the most secure way to communicate when there are no phones is face-to-face (F2F). However, F2F limits everything to proximity specific. At best, it is line of sight communication with hand signs, but more often this will be getting into audible range. Unfortunately, yelling secret info is not in our best interest so we are talking huddle distance. There are circumstances and situations in which this approach makes the most sense based on the needs of the moment. At other times, it places to high a burden on the people involved in comparison in terms of the risks and the time it takes to find people and share information. Albeit, sometimes there is just no avoiding needing to rely on F2F because comms have failed or been hijacked. This is something that happened at Standing Rock in 2016. The state shut down the cell service around the camp while setting up towers for themselves. Then we starting getting reports about mini-drones, the size of large insects, spying on conversations. Either way, take stock of what you need and what you are attempting to accomplish and make decisions about how you and your people will approach the situation before you start, but prepare to be and remain flexible as you may need to adapt in real-time.
The Other Risks
As if the issue with our phones, computers and other devices were not enough, we must also be aware, attuned, and prepared to deal with Mass Surveillance. Over the last twenty to twenty-five years, really since 9-11, the united snakes has dramatically turned up its surveillance engine. Over the last five years it has been kicked into high gear. If you live, work, study, play, or visit any urban center in the US, it is nearly impossible to not be under surveillance of some sort and tracked. This poses serious problems for activists, their supporters, and in particular for the currently targeted groups of people, people who are thought to be migrants and our LGBTQIA+ community members.
The feds are tapping local surveillance networks:
- CCTV footage, from both public and private (commercial & residential) like Ring Doorbells (Amazon), FLOCK, AXON, etc…
- Acoustic Gunshot Location Systems (AGLS) like ShotSpotter that records audio and triangulates location
- Automatic License Plate Readers (ALPRs), ping locations and can track travel and habits (usual routes, link with other people) which, are either stationary cameras or mounted on/in police vehicles
- Local traffic and ticketing cameras
- The Real Time Crime Center (RTCC) which is a hub for the collection and analyzation of surveillance information usually under the control of the local police
- DMVs & DOLs are both sharing data, which makes it easier to target individuals and groups via the ALPR systems
Governments, their departments and agencies, and the corporations who were pulling their strings all claimed that this technology was benign, that it was to be used only in worst case scenarios (like the pandemic or if more planes are flown into buildings), and that it would never unjustly be turned on the public for say, witch hunts. Yet, here we are living out the circumstances of a dystopian science fiction story about the panopticon.
The system is being used to track and control dissidents, migrants, activists and organizers, resisters, our LGBTQIA+ community members, and people seeking gender affirming and reproductive care.
No one is omitted and no one is secure because at anytime the regime in power can access the archive and present a ‘story’ about anyone (psyops). Something sold to the people as something necessary to ensure safety under one context with a particular set of circumstances and agreements, has been shifted to another context in which both the enemies and the objectives are fluid and forever changing. We are living in times when everyone is viable to, and anyone can potentially be labeled a ‘terrorist‘ and thus justifying the full weight of the digital weapon of surveillance and the other forms of state repression.
Additionally, we need to be cognizant of Artificial Intelligence (AI) and corporations like Palantir, with the facial, ear, eye, object, and even gait (i.e., how a person walks) identification and analytical technology. Palantir as a prime example holds contracts with police departments around the country; the Department of Defense (DOD); the Internal Revenue Service (IRS); multiple financial institutions; hospitals and health care systems both domestic and abroad; the Social Security Administration (SSA); the Central Intelligence Agency (CIA); the Department of Education (DOE); the National Security Administration (NSA); voting records; and the Federal Bureau of Investigation (FBI); among many other institutions such as Medicaid and Medicare, which it is using information from under its contract with Immigration and Customs Enforcement (ICE) to hunt and track down migrants. Information thought to be private, secure, and protected both morally and under statute has been placed at the disposal of a technocratic corporation. More glaring are two of Palantir’s objectives: one, to become the US government’s “central operating system” and two, to use technology as an alternative to politics to shape the world how they see fit.
The only things we are missing are the precogs of Minority Report, the central hub with the three laws of I-Robot, the thought police of 1984, and the Terminator. But worry, because they’re getting close.
Joking aside, what this means as a tangible example is that a person can be tracked from the moment they leave there home all the way to their destination, and depending on the destination, the entire time they are there. Additionally, a person is likely even being tracked and monitored while they are at home. Case in point, the mass surveillance devices most of us carry with us twenty-four hours a day in our pockets and bring them to bed with us, our phones. Include with that Ring Doorbells (or similar devices) which have both video and audio capacity, Alexa or Siri with at least audio capacity, connected sex toys, connected appliances, ad infinitum all have surveillance capabilities, and transmit data. So, not only is a person tracked as they move through town, but all throughout the day, even while at home. This information is then recorded, tagged, and stored. In this case, even when we buy the product we are still the product.
Now imagine that the destination is known to provide reproductive care or to provide culturally relevant services to people who have connections with countries where people are migrating to the US from. Since the location is flagged, so too, are all who patron the institution. In another example, the DOL shares name, address, and license plate information with ICE and they feed it into their Palantir system, which taps into the RTCC to access the ALPR data of migrants. They then track their movements through the system and cross-reference the ALPR data with CCTV footage from which they grab current images so they can create a profile and a target. This is the epitome of a system that is not benign. It is also not being used to accomplish what they sold it to the people claiming, namely, that it was to track and prevent “terrorist” attacks, like the Trade Towers or the bombing of a building. Not this perverted twist of logic that the united snakes secretary of stolen-land insecurity, Kristi Noem, keeps spewing to rationalize their human rights violations, as in the tragic murders of Renee Good and Alex Pretti, in Minneapolis in recent weeks, may they both rest in power. They are doing everything they can attempting to normalize the system and their behavior, like if they say it enough times then it will become true.
Another insidious technology being used ICE agents is called, Mobile Fortify, an app they have on their phones and use it to scan a person’s face, whereafter they are able to search government databases with the images of over 200 million people. Remember the Department of Government Efficiency (DOGE) and Elon Musk in 2025? Well, Musk, via DOGE, with Palantir built a Master Database to surveil and track people. It is not clear where all the data has come from for the app and database, but a strong educated guess is that they are pulling from many sources, the Prison Industrial Complex (PIC) being one of them, but also many connected to the departments and institutions named above in the section on Palantir. This means, not only the people labeled “criminal” or “migrant” are in this system, not that either of those categories are just. Mass Incarceration, which includes both mass surveillance and ICE Detention facilities (using that term only as a common reference, these are neo-internment camps), evolved as the ruling class of amerikkka determined Black, Brown, impoverished, LGBTQIA+ people to be “surplus labor” and thus “surplus community” post globalization. It is not only those whom this regime has classified as an “enemy” of the state, and whom the state has worked to shape the narrative around, who are in this system. Mobil Fortify has a database of over 200 million people, and there is only approximately 342 million people in the US.
All of this is happening in real-time to our neighbors and community members, and to us, right now. If you are not currently the target, all that means is that you have not become a threat to their hegemony, yet.
In most urban centers that have built the infrastructure for Mass Surveillance there is little to no means of escaping the reaches of the panopticon. There is not a series of underground tunnels that will get us all to where we want to go. The public transportation system is packed full of cameras. There are cameras at nearly every major intersection, on the doors of most homes and apartments, and on almost every business. Between the CCTV and the ALPRs it is nearly impossible to drive yourself, and even the ride shares are tracked and linked to individuals, both the driver and the passenger. Walking into an event or an action encounters the same problems via the CCTV. There does not seem to be a good escape from being observed. This too, may actually impact someone’s ability to privately secure a burner phone.
If we cannot avoid detection, then the only means of defense we have is to be selective about what they detect.
There is camera obfuscating and AI confusing clothing that can be worn, which will make the images blurry or fuzzy, and/or cause the recognition software to be uncertain about the actual face of the person. Face masks, glasses, and head coverings also go a long way. The AI recognition software is advancing very quickly and they are making positive identifications from eyes and earlobes, these days. Having clothing that is only brought out when you aim to be at an action may also be a wise idea. But don’t forget that the recognition software is also programmed to identify how people walk, or that even covered up the cameras can be used to track a person matching a particular description through the system, and they can work both forward and backward after the fact. While these steps and others like them will not stop a motivated authoritarian regime or technocratic corporation, and they may only serve to slow them down, they are not without their merit.
Activists, organizers, and others who are targeted must also be worried about doxing. Doxing is when nefarious individuals or groups garner information about a person and publicize this in some way to humiliate, intimidate, or otherwise harm them. Much of the information from the Mass Surveillance infrastructure can be accessed via public information requests, or simply tapping their homies, the police, who have been caught sharing information on the sly. Much of the rest of the information used in doxing people tend to volunteer unknowingly, but that will be addressed more in the next section. Being covered up provides some protection from random nefarious opposition agents from using their own facial recognition software (or efforts) and making links to other information we did not think was harmful to be out in the public, like on social media.
Earlier, I mentioned a few topics that I promised to return to and Social Media sits square in the heart of it. One of those topics concerned being able to trust the messages that are sent to us. Another topic regarded the infiltration of our spaces either digital of physical. Social Media, as an engine all its own without things like SOMEX, i.e., the Social Media Exploitation Program, or Psyops, is a cluster fuck of social programming that is dangerous and has the power to corrupt everything we do.
Social Media was sold to our civilization as a unilaterally open and transparent tool, when in fact everything about the experience is curated to the individual. Social Media functions like and activates the same regions in the brain that drugs activate. Social Media is a drug. From the way the buttons and swipes function–like a slot machine, to getting “likes” or “hearts” which provide endorphin hits, to the dissonant frequencies of the notification sounds which never seem to stop that activate the amygdala, the part of the brain in the limbic system responsible for fight or flight responses, social media is designed to get and keep us hooked. As someone who fought through several addictions and who has been sober from drugs and alcohol for a quarter century now, believe me when I tell you, even though you probably found this article through social media, which means that you are on it and probably not feeling at all comfortable about what I am writing, an addicted person is not functioning with their full rational mind about the thing they are addicted to. There are really only two things which refers to its consumers as “users,” and that drugs and social media. As if this wasn’t bad enough, the systems are also designed to garner micro agreements that function like a “foot-in-the-door” for much larger commitments down the road, usually related to some product their clients are pushing. The truth is that the users of social media are the product.
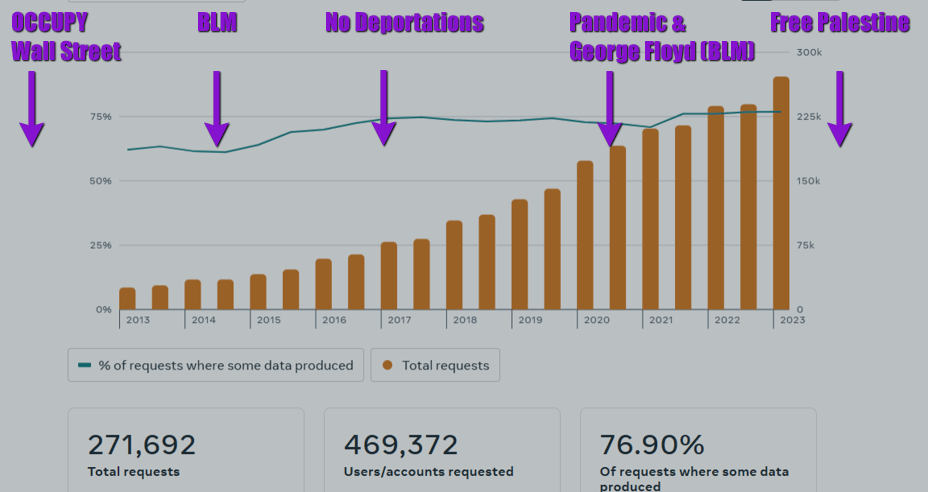
The graphic above details the growing number of law enforcement requests to and the number of request satisfied over the decade between 2013 and 2023 by Facebook, which many of us aptly call FedBook. Other social media platforms have experienced similar trends and share similar information. Google is also notorious for this and so is Zoom. It is not only social media that is doing it. The authorities have found internet platforms such as these to be literal treasure troves of information that people readily volunteer.
People share where they go to school, where they live, where they work, what they do for fun, and who they do all these things with. People share their happy times, their sad times, and photos of all the times. People check-in at places alerting the whole world that they are not home. People share their politics and their religious or spiritual sentiments, and their relationship statuses as they change. Most of these sites, although not all, are multimedia platforms wherein people are sharing photos, videos, and audio recordings of literally everything. Dating apps are some of the most intrusive apps there are. They persuade people to upload the most personal information about themselves in the hopes of garnering some connection, and they almost all require use of an access to the location function of the device being used. Apps like Facebook, Instagram, Twitter, and TikTok that most people have on their phones and use to remain connected with friends and allies and to share the most current affairs as they happen; i.e., live streaming an event, all have settings in the apps defaulted to track location, and accessing microphones and cameras at will.
The police and the feds have been pilfering the digital places we gather and store information for about as long as they have existed because why not, right? In tangible terms, how this might play out is the feds are building a case about some protest but they do not have footage (yet) and they need ‘motive’ to really build a case. So, they turn to Facebook to identify all the people who were in a particular location at a specific time and then they investigate all the people in that pool. Or they pull all the names of the participants in some forum on some site and use that as the foundation of their investigations. Now add to that how the Arab Spring, the Occupy Movement, and the Black Lives Matter Movement pretty much all got kicked off and were largely networked on social media platforms. I can still remember BLM Facebook chats with like 300 people planning actions. I do not even want to venture a guess at how many cops were in those chats, but be damned if they were not always there and ready before we showed up. Social media is a leakage point and a massive vulnerability for everyone, but especially for organizers, activists, and resisters.
Another dangerous element of social media, which is quickly spreading throughout the internet is the curated world. Content creators in the music and the movement alike have often referred to this as beating the algorithm, that is, reaching outside of their customary audience to new people. However, it is an intentional move by those who manage the corporations that control social media to pool people into like minded categories and to even curate their searches. This practice is so insidious that two people with different histories can search for the same thing with verbatim text and receive completely different responses. The reason for this tactic is that by grouping people together with people who think like them is to foster an agreement tree. Going back to the “foot-in-the-door” micro agreements above and linking these two agreement trees together, a person is psychologically moved into a position of agreement. This is a very effective strategy for selling products. It is also an effective strategy for deploying Psyops, that, is political manipulation.
The point of Psyops is to engineer one’s perception of reality. George Orwell, the author of “1984,” spoke about how the hegemony has worked tirelessly to get the people to believe that war is peace. This War on Drugs is to bring peace to our communities. This War on Terror is to bring peace to our world. The draconian hunting and expulsion of suspected migrants is peace. Trump is “the President of Peace.”1 These are engineered versions of reality tailored to control the population. Now of course, the hegemony has more than social media at its disposal, so we must all be weary of the news, sitcoms, movies, tabloids, magazines, social media, and essentially anywhere we might get anything close to real-time information. It is not ubiquitous and it is not all the time, but it is so prevalent that we cannot afford to passively consume information any longer. For a much deeper dive on Psyops you can check out Chase Hughes on YouTube. One very important concept Hughes highlights is how a Psyops agent will attempt use Cognitive Dissonance (that is, try to create an inconsistency between who we believe ourselves to be and something we are doing) and the “shifting of the context” surrounding an idea or an issue. In both cases, neither need or will likely happen at the same time, but at some point they are drawn together and weaponized to manipulate both individuals and large groups of people. For example, the cognitive dissonance element might be, “only a person who disagrees with improving the safety of our communities would not want surveillance cameras installed in their neighborhood.” The shifting context element might be that when the argument was first made there was a spike in gun violence, but now the cameras are being used to hunt and capture non-violent people suspected of being migrants. Psyops is often a long-game strategy, but it also has short-term elements. Here is a list of logical fallacies Hughes warned to be mindful of because of how frequently they are used to manipulate people’s perception and thus their behavior:
- Appeal to Emotion (fear, anger, hope)
- Strawman Argument (misrepresent argument to attack it)
- Bandwagon Fallacy (good/true because everyone supports it)
- False Dilemma (presents only two extreme options, ignores alternatives)
- Ad Hominem (attack person, not the argument)
- Appeal to Authority (claimed true because an authority figure said it)
- Slippery Slope (one action leads to an extreme outcome)
- Hasty Generalization (broad claims with little evidence)
- Red Herring (distracting people with irrelevant information)
- False Equivalence (compares things as equals when not at all true)
Which brings us to the the FBI program, SOMEX. The objectives of this program include collecting evidence, infiltrating groups, sowing disinformation and creating rifts between groups and within groups. Most of our groups and organizations, as well as, most of us access and utilize some form of social media and have for a long time. There are benefits to being our own marketing and to being where so many people are. This is how we find like minded people and groups and how we mobilize for events and actions. It is where we get to share our stories and facilitate political discourses. At the same time it is also surrendering lots of surveillance information about ourselves and our groups. Many social media sites are built to function best with photos and videos, which in turn have tons of metadata baked into the files. When social media started and when most of us start using social media (at whatever age) there was not a safety guide for what to watch for or how someone or some group might peruse our entire profile wall of posts piecing together information to use against us or exploit our weaknesses, but it happens.
It is also a prime environment wherein someone can create an avatar that looks attractive or sympathetic in the world of avatars who makes friends with one or some of the members of our group. They see our events, they join, and start working their way in. From there, they get added to more private meetings and chats and now they are on the move to get sensitive information and they have access to sow misinformation. This is going on, it was proved to have happened in Seattle when the Capital Hill Autonomous Zone was in motion, and decades before the advent of the internet, COINTELPRO, another program under the FBI and J. Edgar Hoover, used the seed and sow tactic to foment discord among the chapters of the Black Panther Party. An uncomfortable historical fact about the Seattle Police Department is that they went to the Central District and claimed that people from the South End were talking trash about them. They filmed the response and took it to the people in the South End and filmed their response after showing it to them. The police then brought back the video of the South End response to the Central District and there has been beef between what became rival gangs ever since.
We must be especially cautious with how we handle the information we receive, whether it is from the news, social media, or people we think we know and trust. Where did the information come from? Has the information been vetted? Why is the information coming to us now? Both people and AI have been shown to make deep fakes, and sometimes they are meant as jokes to begin with, but they can catch steam. If we are hearing rumors about a comrade, are we going to our comrade to verify, or are we just taking word as bond and allowing the discord to spread? Screenshots can be simulated by someone with enough skill and patience. How can they be taken as proof by themselves? What reality is this information presenting to us? What was the context in which the thing first showed up and how has the context shifted? Is there anything about this information or the way it was presented that even hints at manipulation? If we accept the information presented to us as fact, who stands to benefit and why? In fact, we are currently seeing lots of misinformation and misdirection targeted to interrupt migrant defense rapid response networks, and even blue lives matter piped up and had some snarky ass remarks to share about it after the fact.
Dis-Information has an can be a very destabilizing tactic used against us and through us. We must be vigilant and on guard against being manipulated by the hegemony or its agents of chaos.
For all of its benefits, Social Media exposes us to tremendous vulnerability. If it is to be used then it must be done with vigilant caution because it poses more of a threat to our security than a benefit to our mission. I recommend that no one person be responsible for the social media indefinitely and that there is a rotation of who is responsible. I further recommend schedule detox rotations so our people have an opportunity to purge the Psyops sludge from our minds. Collective care and rest are revolutionary and they both serve to strengthen our security. This lends itself to working with a sense of urgency instead of from a sense of crisis.
Conclusion
This hegemonic, authoritarian, fascist, technocratic regime has been hard at work for decades building the infrastructure of Mass Surveillance and control around us. True, we have our work cut out for us, if we intend to resist amidst what seems to be overwhelming repression. So many of the technologies and software that have become almost standard operating procedures in our lives and work can be turned against us seemingly with but the stroke of a few keys. And yet, resistance is neither hopeless, nor is it pointless. Quite the opposite, resistance is essential. And while it is unlikely that we are to experience some decisive victory at the end of some pitched battle like in the movies, and like most new recruits into the resistance struggle seem to believe, we are nonetheless, the continual balance to the equation.
There is nothing new about a hegemonic tyrant repressing and oppressing the people.
There is also nothing new about grassroots movements overthrowing tyrants. The story of us and how we got here is replete with people after people, story after story of how that was accomplished.
Frederick Douglass said “Power concedes nothing without a demand” but, only after he said that we must be willing to risk everything, even our own lives for our own freedom. That is the level of determination and conviction which our predecessors and ancestors brought to their resistance struggles, and so must we.
One thing we know for certain, is that the hegemony is afraid of the resistance. It is customary for one side to develop a weapon that provides them with an advantage and then for the other side to develop a defense which mitigates that advantage. Then for the latter side to develop a weapon or tactic that provides them an advantage over the former and so on and so forth. This current evolution of the weapon of Mass Surveillance is but another rung on the ladder of the struggle that I believe is arching toward justice. They developed it because of how successful and transformational the resistance struggles were in the 1950s, 1960s, and 1970s. That is a testament to those who came before us, however incomplete we may feel these work was at times. The current regime would not invest some much time, energy, and resources into quelling our resistance by working rob us of our will to fight, or keep such a watchful eye on us, or steal the programs and practices we create and try to claim them like they are responsible for them. We are actually much more powerful than most of us give ourselves credit for.
We have the measures and the means to mount a defense against this weapon of surveillance that is part of the mass incarceration infrastructure, while we work toward dismantling it, but we must first understand our opponents and their tools. That is what I have attempted to accomplish with this article / guide. I believe that it is important that as many of our people are informed about the current state of things as possible and that we are working toward getting our people ready for what is coming next. So, I pulled together this compendium of experiences and learnings from book readings, research, and OTG experience being an activist, organizer, and resister for more than a decade now. It is my hope that you find it helpful and useful, and worth sharing with other who may also benefit. Of course, as is often the case, is that almost as soon as we are able to learn about something well enough to comprehend and share it in a meaningful way, there is already new technology, practices, and tools out there that is smarter, faster, and more invasive than we have written about. That is why this has been a career-long exercise for me and it will continue to be. It is also why this article will be updated from time to time, so as to reflect the evolving environment we find ourselves. So, I invite you to continue along your own journey and to keep improving your knowledge and understanding of the tools, weapons, and practices used against us.
In short, there is no real and meaningful way to prevent tracking. We as a people need to accept that even with the best practices we will never be completely protected from discovery and that there is no such thing as “safe” when resisting fascism. Yet, regardless of that, I still believe we should be defending our community, both the people and the places we call home from those who seek to destroy it.
ALL POWER TO THE PEOPLE
Last Updated: January 2026
- National Security Strategy of the United States of America November 2025 (p. 8) https://www.whitehouse.gov/wp-content/uploads/2025/12/2025-National-Security-Strategy.pdf ↩︎
Leave a comment